When “risk assessment” is mentioned in the information technology or information security crowd, IT risk assessment is typically the first thing that comes to mind, probably because it has been around the longest, at least from a regulatory-guidance perspective.
As important and measurable as the IT risk assessment can be, it is only part of the equation for assessing risk. Relying solely on a very granular, asset-based risk assessment to make decisions for your entire organization is not practical or logical.
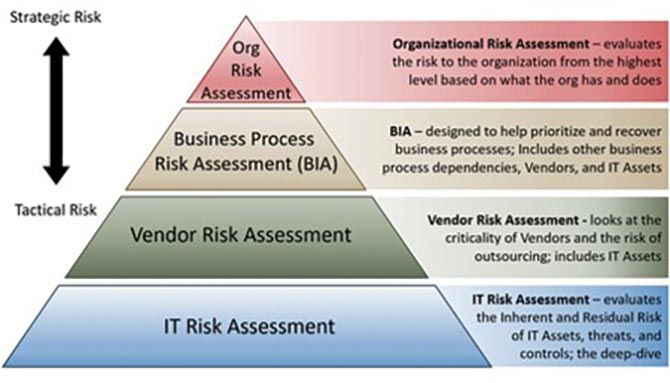
It is recommended that different tiers of risk assessments are necessary for organizations to understand interconnected risks. The tiers range from the foundational IT risk assessment to the departmental business process risk assessment and the strategic organizational risk assessment.
How Do These Risk Assessments Work Together?
The IT risk assessment is the foundational, tactical, day-to-day operational risk assessment that takes a deep dive into controls associated with specific IT systems and assets. An organization must understand what it has, how those IT assets are being protected, and where its next information security dollar should be spent. IT risk assessment should look at numerous different types of controls, including asset-specific controls, network controls, physical controls, and organizational controls.
IT risk assessment then feeds the vendor risk assessment, as our vendors not only represent risk themselves but also provide your IT systems and assets, likely hosting many of those IT systems and assets for your organization today. It’s important to rate your vendors on the health of their organizations and the IT systems and assets they provide to you. In many cases, if the vendor is hosting these IT assets on your behalf, they will have the ability and responsibility to implement risk-mitigating controls more so than you.
IT risk assessment and vendor risk assessment then roll into the business impact analysis (BIA). The BIA is a business-process risk assessment designed to help your organization understand the importance and recovery priority for each business process. But to have a functional business process, your organization will require specific IT assets and the vendors providing you with those IT assets and services.
Most business processes depend on specific IT assets, vendors, and sometimes other processes being restored before that particular business process can regain functionality.
The top tier of risk assessment is the organizational risk assessment. This type of assessment evaluates the entire organization from the top down based on the products and services the organization offers to clients or uses to perform business functions.
All four risk assessments must work together to build a strong information security program at your organization. Each risk assessment is going to provide distinct, unique value while each being interconnected with one another. If your risk assessments can work together to truly help you make better, more informed decisions, you’ve got something of real value.
Making Better Decisions
Suppose your IT risk assessment doesn’t help you to continuously improve security maturity or make decisions. In that case, you’re merely checking the risk assessment box to appease regulators and not using your risk assessment(s) to improve your organization.
So how do you make better decisions based on the risk assessment?
It all starts with the IT risk assessment. It must be measurable. Once you understand how much risk you have and how much risk you’re mitigating, you can start to set risk mitigation goals.
Determining those acceptable levels of risk will help you determine which IT assets are meeting risk goals and what else you should be doing to mitigate risk around those IT assets, and where you should spend your next information security dollar.
When tasked with creating a risk assessment, it can be seen as a daunting and pointless task. Comprehensive, measurable, and repeatable risk assessments should be used to help make better decisions. Without a detailed framework, money spent on information security is akin to throwing darts at a board. Without a goal, how do we know when we’ve reached it?
For more information, contact Robb Nielsen at 605-251-7375 or robb.nielsen@sbscyber.com. SBS helps business leaders identify and understand cybersecurity risks to make more informed and proactive business decisions. Learn more at www.sbscyber.com.







