As data breaches continue to trend up, organizations are spending more money and resources to ensure they have the appropriate solutions in place to prevent attacks without disrupting normal business. All organizations should consider the following topics as part of an information security program review.
- Ransomware Awareness
The CSBS recently updated the Ransomware Self-Assessment Tool (R-SAT) to version 2.0 due to evolutions in the ransomware threat environment, bad actor tactics, and changes in environments and controls. The R-SAT provides significant advantages by raising awareness about ransomware risks, identifying security gaps and giving executive management and the board of directors the information they need to make informed decisions and allocate resources appropriately. It also assists auditors, consultants and examiners in evaluating security practices and incorporates lessons learned from organizations that have experienced ransomware attacks. - Board Cybersecurity Training
An organization’s board of directors is ultimately responsible for its overall security. Without a solid grasp of cybersecurity, the board may make decisions that inadvertently weaken the organization’s security posture and lead to insufficient budget allocation for cybersecurity initiatives. Additionally, a lack of understanding can result in security strategies not aligning with overall business objectives, as well as underestimation of cybersecurity risks, leading to inadequate risk management and crisis response plans. - Firewall Reporting and Monitoring
To mitigate the risks of vendor firewall management, it is important to implement appropriate controls, including defining roles, responsibilities and expectations in written contracts to eliminate any questions as to who is doing what. Periodic security audits of the vendor’s practices should be conducted as part of your vendor management program.
Administrative access to the firewall should be limited to authorized personnel only, and require strong authentication mechanisms, such as MFA and individual authentication (no shared accounts). Oversight should include receipt and review of comprehensive logs or read-only access, at a minimum, to monitor these logs for suspicious activities or policy violations. - Multi-Factor Authentication (MFA)
Implementing MFA is a key defense strategy, adding an essential layer of security by requiring two or more verification factors. Enhancing network security with MFA solutions helps increase data-center security, boosts cloud security for a safer remote working environment and minimizes cybersecurity threats.
Additional controls surrounding administrative access to directory services, network backup environments, network infrastructure, organization’s endpoints/servers, remote access (employees and vendors) and firewall management are recommended. Many cybersecurity insurance vendors now require organizations to complete a self-attestation to renew policies. Included within the attestation is the verification of multi-factor authentication for remote access users and administrative users. - Vendor Management Program
The vendor management program continues to evolve and requires diligent monitoring and research, especially for those vendors deemed critical to operations. Adhering to FFIEC Guidance and Interagency Guidance ensures comprehensive risk evaluation in vendor relationships, comprised of due diligence procedures, acquisition procedures, defined vendor risk classifications, annual risk assessments, presentation of critical vendors to an authorized committee and adequate contract review procedures.
Organizations should adopt a comprehensive vendor management program to address vendor risks and ensure adherence to legal and regulatory standards. - Microsoft 365 Controls Assessment
An independent assessment is crucial for identifying and mitigating potential cyber threats within the Microsoft 365 environment. The independent assessment should evaluate the environment and ensure the organization has implemented appropriate controls to mitigate risks, including malware, third-party app access, data loss prevention, external sharing, advanced threat protection and permissions.
Common security gaps within the Microsoft 365 environment include overly privileged administrator roles, incorrectly implemented multi-factor authentication, inadequate admin center settings, audit log and activity log neglect, and authorization misconfiguration. - Adequate Backups and Testing
Implementing various disaster recovery measures to prevent and mitigate ransomware attacks is important, including keeping multiple backups on and off-site, replicating critical data, encrypting data and air-gapped backups. Regular testing of backup procedures is essential for ensuring data recoverability in the event of an attack. An air-gapped backup is not connected to a network, so it cannot be reached by hackers, as many ransomware variants attempt to find and delete any accessible backups. Maintaining offline, current backups is critical because there is no need to pay a ransom for data that is readily accessible to your organization.
Regularly testing and validating backup processes can give an organization confidence in its ability to restore data in the event of an emergency. This includes restoration testing, functional failover testing — spinning up critical backup servers, and other emergency preparedness testing (tabletop exercises, simulations, etc.). - Bank Protection Act of 1968
The shift towards remote audits and examinations poses challenges for physical security verification, which often relies on videos or photographs for assessment. To bolster physical security measures, it is recommended that a dedicated security officer be appointed to oversee the comprehensive implementation of the security program and deliver an annual security report to the board of directors. - Segregation of Information Security from Information Technology
Once a financial institution reaches $750 million in assets, the regulatory and external audit scrutiny will increase surrounding the segregation of roles associated with information security and information technology. The information security officer should be independent of IT operations staff and should not report to IT operations management.
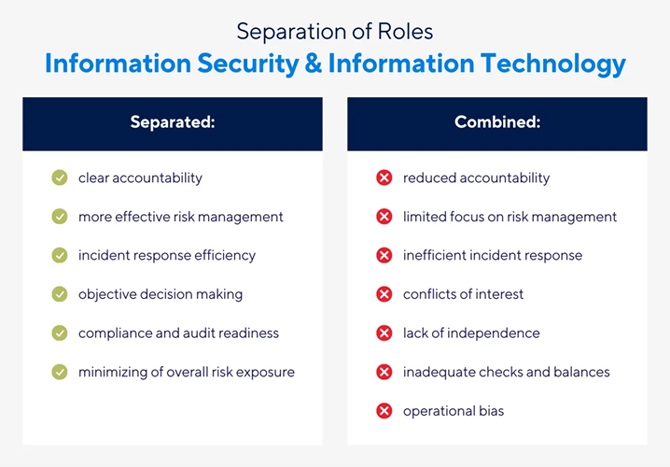
- New/Updated Policies
The following policies should be documented within an information security program, and some have become formal recommendations by examiners and regulators within the last 12 months:- End-of-Life (EOL) Policy
- Imaging Policy
- ATM/Debit Card Management Policy
- Instant Issue Policy
- Internet Banking Policy
These enhancements aim to bolster the institution’s security posture, ensuring comprehensive coverage of physical and digital security aspects in alignment with evolving regulatory standards and cyber threat landscapes.









